Custom DNS
Overview
Custom DNS settings can help prevent DNS leaks and enhance your privacy when using proxies. Some proxy providers might not have their own DNS servers or could potentially leak your actual DNS server IP address.
Privacy Risk
Using affiliate DNS servers (like Google DNS for Google services) might expose your real IP address.
Testing DNS Leaks
To verify your DNS configuration is secure, you can use these testing tools:
Popular DNS Providers
Choose from these widely-used DNS providers. Consider selecting a local DNS server matching your external IP location for better authenticity.
| Provider | Primary DNS | Secondary DNS |
|---|---|---|
| Alternate DNS | 76.76.19.19 | 76.223.122.150 |
| AdGuard DNS | 94.140.14.14 | 94.140.15.15 |
| Cloudflare | 1.1.1.1 | 1.0.0.1 |
| CleanBrowsing | 185.228.168.9 | 185.228.169.9 |
| Control D | 76.76.2.0 | 76.76.10.0 |
| 8.8.8.8 | 8.8.4.4 | |
| Level3 | 209.244.0.3 | 209.244.0.4 |
| Neustar | 156.154.70.5 | 156.157.71.5 |
| OpenDNS | 208.67.222.222 | 208.67.220.220 |
| Oracle Dyn | 216.146.35.35 | 216.146.36.36 |
| Quad9 | 9.9.9.9 | 149.112.112.112 |
Setting Up Custom DNS
- Mimic
- Stealthfox
Configuration Steps
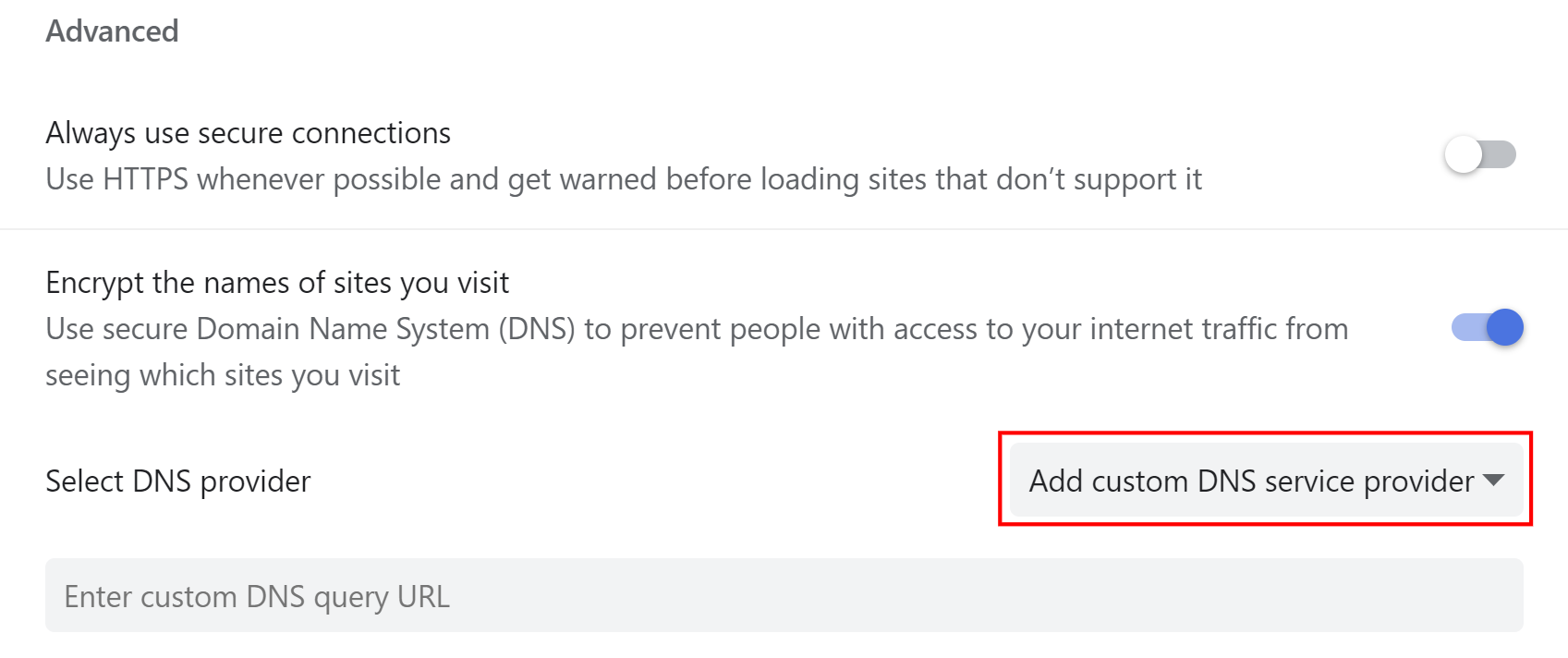
- Navigate to
chrome://settings/security - Scroll to the "Advanced" section
- Enable "Encrypt the names of sites you visit"
- Select "Add custom DNS service provider" from the dropdown
- Enter your chosen DNS query URL
Configuration Steps
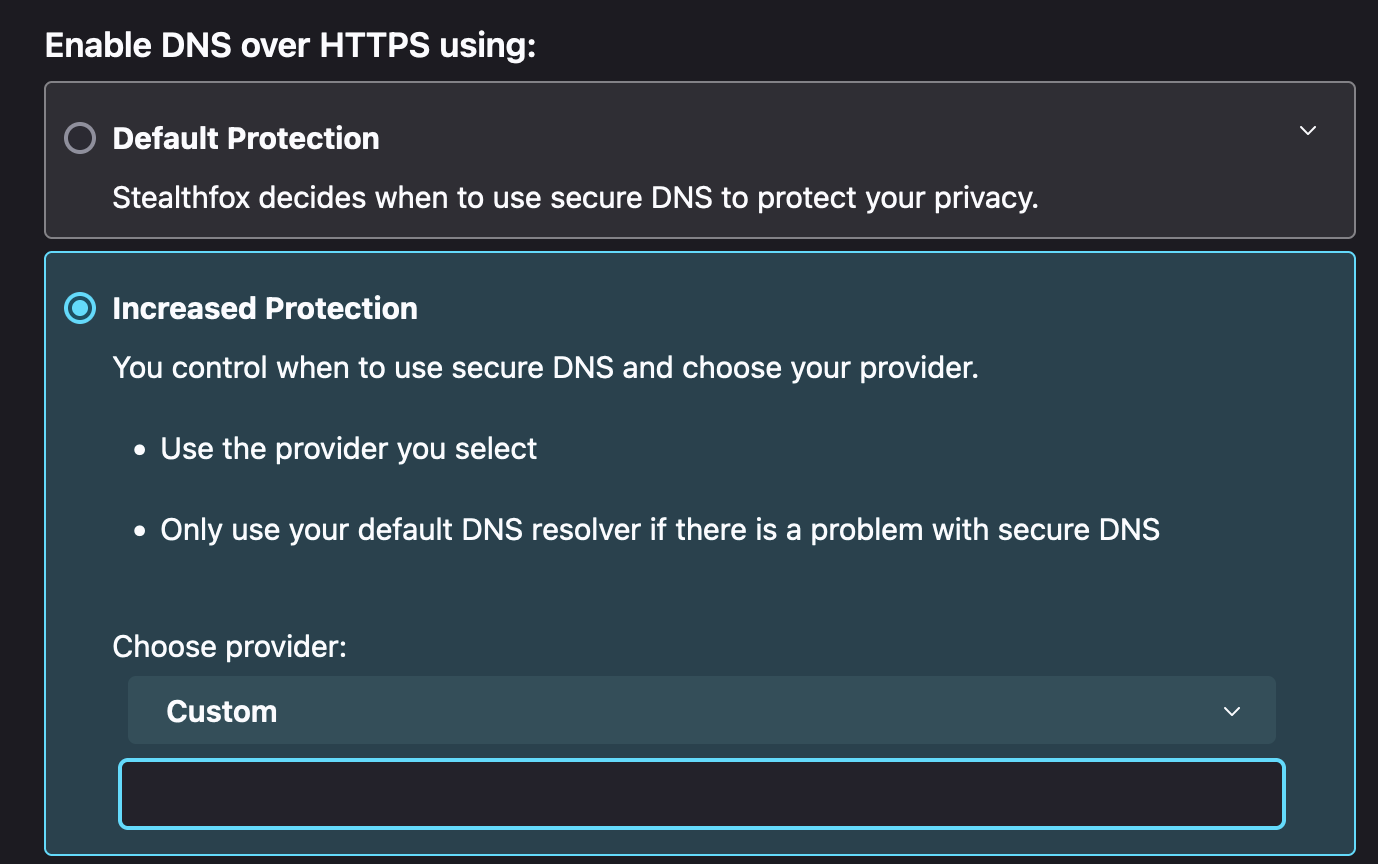
- Go to
about:preferences#privacy - Scroll to the bottom
- Enable "Enable DNS over HTTPS using increased protection"
- Select "Custom" from the dropdown menu
- Input your DNS server IP
Recommendation
For optimal privacy, choose a DNS provider that aligns with your proxy's location.