Data Safety in Indigo
Our Commitment to Security
High security standards are our top priority across all Indigo products. We implement paranoid-level security systems to ensure your data remains protected at all times.
Password Security Architecture
How We Protect Your Master Password
Your account password is never transmitted or stored in plain text. We use a multi-layer encryption approach:
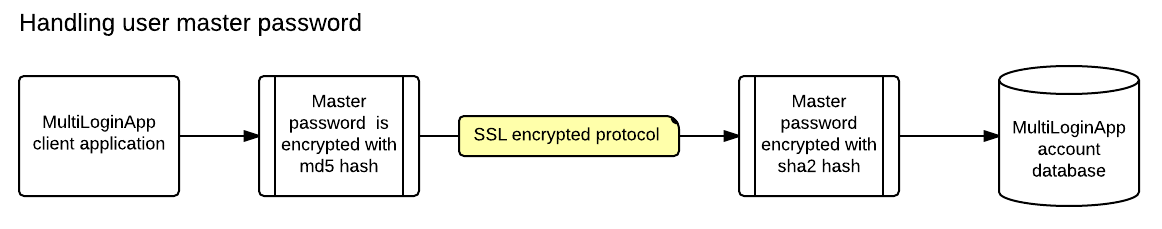
Using a sample password: Rlvy71kswtWMjxcEFsNS
- Original:
Rlvy71kswtWMjxcEFsNS - After MD5:
9f9173e04ab6a708adc7fad26897074 - After SHA-2:
f2205505e129ce8ce5f22d524e56f2d4339bc8b312896480d5d6a55cae878de7
Password Best Practices
- Minimum Length: 16 characters
- Composition: Mix of numbers and letters
- Complexity: Include both upper and lowercase letters
Account Data Protection
Cookie Management System
- How It Works
- Security Measures
- First website login generates a unique session cookie
- Indigo securely captures the cookie
- Cookie is encrypted using AES cipher
- Encrypted data is stored in cloud storage
- Individual session encryption
- AES cipher encryption (NSA approved)
- Master password-based encryption
- Secure cloud storage
AES (Advanced Encryption Standard) is approved by the NSA for top-secret information when used in an NSA-approved cryptographic module.
Data Retention Policy
When you stop using Indigo:
- Your data is retained for 3 months after subscription termination
- All data is completely purged after the retention period
- You receive multiple email reminders before deletion
Data security - our top priority
Our team includes only experts in the field of software development. Some of them have more than 8 years of experience in web development and security of Internet banking systems.
We are superior in security to many financial institutions. If you trust your online bank to save your data, rest assured that we can do it even better.
Data Flow Overview
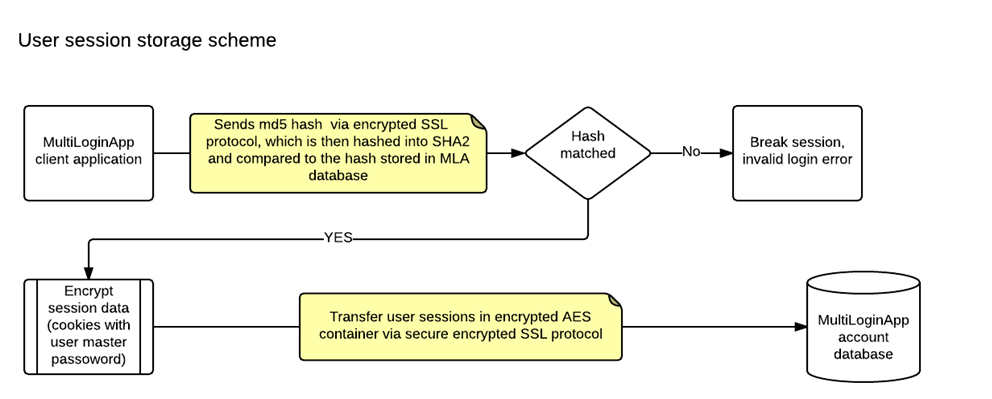
Continuous Protection
Your data security is maintained through:
- Regular security audits
- Continuous monitoring
- Proactive threat detection
- Immediate security patches
While we maintain the highest security standards, always follow security best practices:
- Use strong, unique passwords
- Enable two-factor authentication when available
- Keep your master password private
- Regularly update your security settings